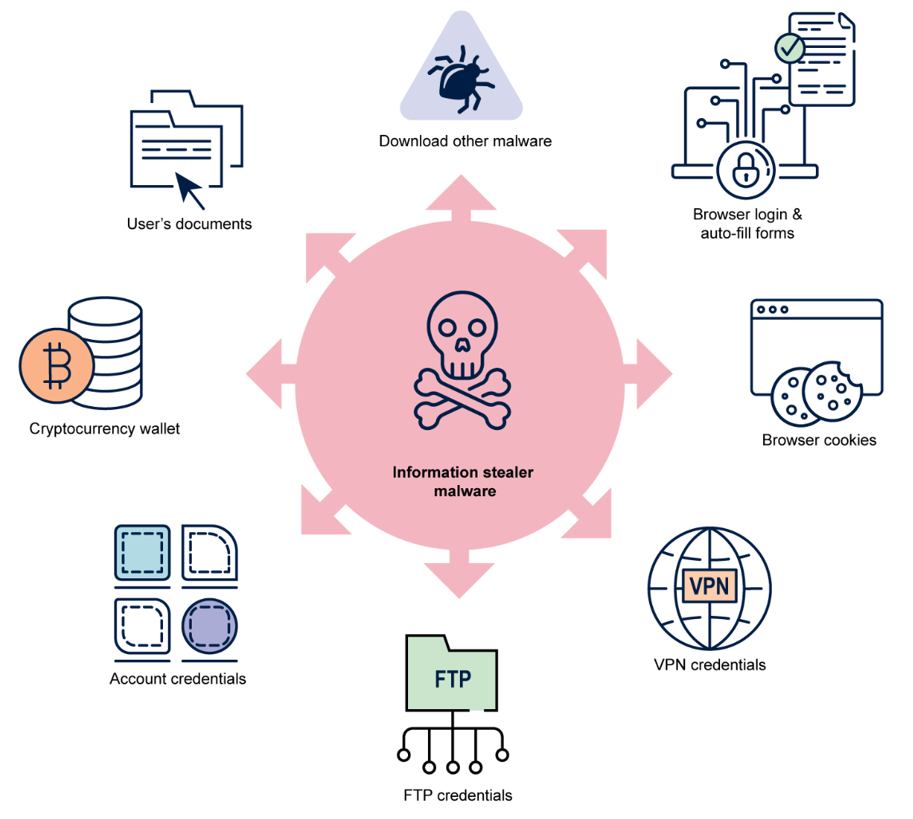
**Unnamed Tool That Steals Files You Never Meant to Share: What You Need to Know** In a digital world where data leaks happen faster than updates, a quiet but growing concern is emerging: invisible file leaks in everyday software. Users across the U.S. are increasingly noticing unexpected "file leaks" during routine tech use—videos, photos, documents, or personal files disappearing without intent. While the cause isn’t always obvious, emerging tools act as silent contributors by harvesting data through shared links, embedded scripts, or unointended file transfers. This isn’t malicious software in the old sense—instead, it’s how routine features expose sensitive data when permissions or privacy safeguards fall short. Recent trends show rising user awareness about digital privacy, driven by high-profile data incidents and growing adoption of hybrid work and smart device ecosystems. Consumers and professionals alike are asking: “How do files get shared beyond my control?” and “Why do trusted apps sometimes take more than intended?” The unnamed file-stealing phenomenon touches on these questions, fueling curious exploration across mobile and desktop platforms. ### How Does the Unnamed File Exposure Happen? At its core, the issue often stems from how applications access and temporarily store data during routine operations. Many apps—especially file-sharing, cloud sync, or social tools—require brief access to user files to enable sync, editing, or embedding. In some cases, files creep into cache, temporary storage, or even shared links unintentionally. Without robust permission controls or user awareness, these exposures become silent leaks. No hacking attack needed—just misconfigured defaults, permissions, or unsecured APIs.
### Common Questions People Ask About File Exposure Risks **Q: Can apps really keep my files longer than intended?** Many apps cache data temporarily for performance, but unclear retention times mean files may stay accessible longer than expected. **Q: Are these exposures intentional or accidental?** Most cases are accidental—features designed for convenience become oversharing paths with weak privacy safeguards. **Q: Can I stop this from happening?** Yes. Review app permissions regularly, use privacy settings, and stay informed about software updates that tighten data handling. **Q: What types of files get exposed?** Commonly, documents, media, cloud backups, and inline exports from shared documents or collaborative tools. ### Opportunities and Realistic Considerations The growing attention reflects a meaningful shift: users now demand clearer control over data flow. For businesses and developers, this highlights a gap—user trust hinges on transparent privacy practices. On a personal level, recognizing subtle risks empowers safer digital habits. However, there’s no single “solution tool.” Awareness, proper settings, and mindful sharing remain powerful defenses. ### Common Misconceptions Debunked Many fear this is a new form of malware—but it’s rarely deliberate software. Instead, it’s a symptom of outdated privacy defaults and complex digital interactions. Consumers should avoid overreacting to every notification about data leaks. Instead, focus on granular app permissions and regular reviews of connected services. ### Who Benefits From Understanding This Exposure? This pattern affects everyone—from freelancers syncing portfolios to small teams sharing client files. It impacts anyone using cloud apps, messaging platforms, or devices with file sync. Transparency here isn’t just about security—it’s about digital dignity in a connected world. ### Stay Informed, Stay Connected Safely Understanding the unnamed file exposure risk isn’t about fear—it’s about control. By learning how data moves, why files slip beyond intent, and how to manage permissions, users reclaim confidence in their digital experiences. Make privacy a habit, not an afterthought. Explore trusted tools that enhance secure sharing, and stay curious—your digital footprint deserves thoughtful attention.
This pattern affects everyone—from freelancers syncing portfolios to small teams sharing client files. It impacts anyone using cloud apps, messaging platforms, or devices with file sync. Transparency here isn’t just about security—it’s about digital dignity in a connected world. ### Stay Informed, Stay Connected Safely Understanding the unnamed file exposure risk isn’t about fear—it’s about control. By learning how data moves, why files slip beyond intent, and how to manage permissions, users reclaim confidence in their digital experiences. Make privacy a habit, not an afterthought. Explore trusted tools that enhance secure sharing, and stay curious—your digital footprint deserves thoughtful attention.
Can Yunexpress Cure Your Travel Woes Forever? Discover the Revolutionary Speed!
Yellowstone Season Two Secrets No One Wants You to See
You Won’t Believe What Happened After Wtov9 Spilled The Truth